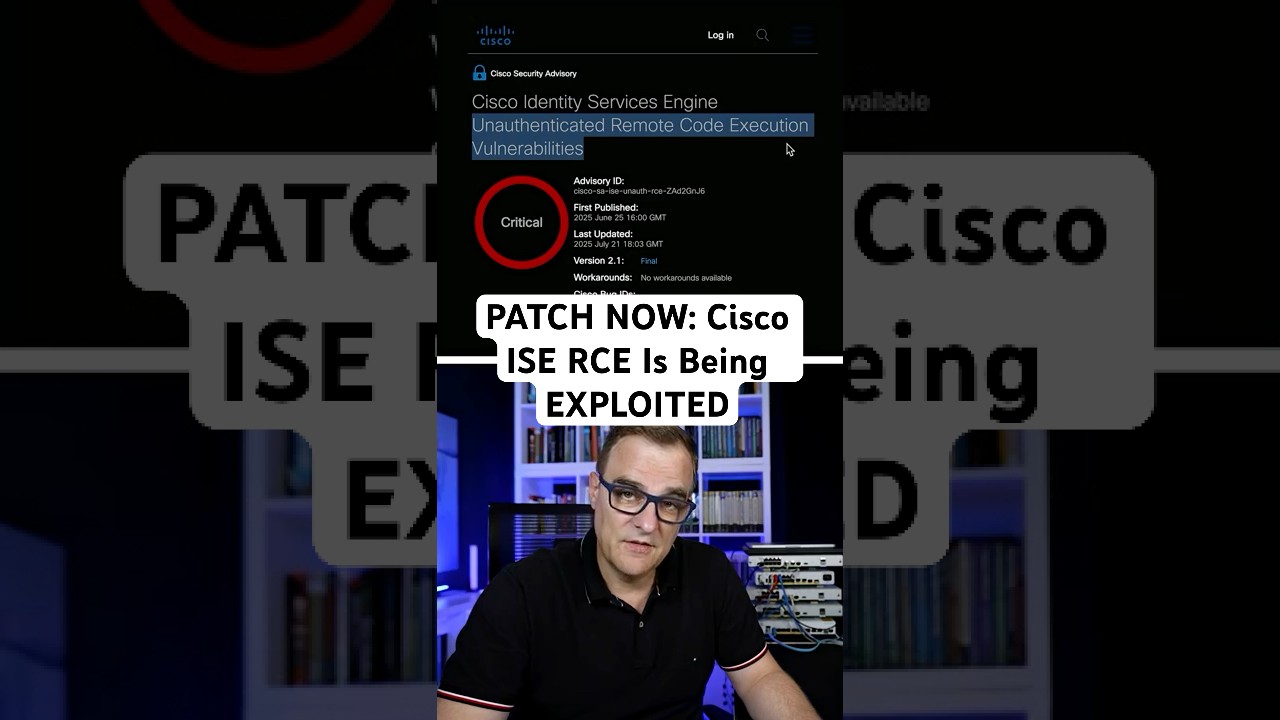
PATCH NOW: Cisco ISE RCE is being exploited
Cisco ISE (Identity Services Engine) has a maximum‑severity (10/10) remote code execution vulnerability, CVE‑2025‑2281, and Cisco says it is already being actively exploited (July 2025). An attacker can submit a crafted API request and gain root on the underlying OS without authentication. There are no workarounds. Multiple independent vulnerabilities are included in the advisory, so you must upgrade to a fixed release immediately.
In this video I explain:
What CVE‑2025‑2281 means for your ISE deployment
Why the bug is unauthenticated and gives root
How the exploit path works (crafted API request, insufficient input validation)
Why there is no workaround
What you should do right now to reduce risk
Action: Check your Cisco ISE version and patch to the fixed release immediately.
#cisco #ise #cve20252281
In this video I explain:
What CVE‑2025‑2281 means for your ISE deployment
Why the bug is unauthenticated and gives root
How the exploit path works (crafted API request, insufficient input validation)
Why there is no workaround
What you should do right now to reduce risk
Action: Check your Cisco ISE version and patch to the fixed release immediately.
#cisco #ise #cve20252281
David Bombal
Want to learn about IT? Want to get ahead in your career? Well, this is the right place!
On this channel, I discuss Linux, Python, Ethical Hacking, Networking, CCNA, Virtualization and other IT related topics.
This YouTube channel has new videos upload...